In the ever-evolving landscape of cybersecurity, the traditional password is facing increasing challenges, prompting a transformative shift toward more secure and user-friendly authentication methods. This transition is spurred by a confluence of factors, ranging from the escalating sophistication of cyberattacks to a heightened awareness of the risks associated with password reuse.
As technology continues to advance, innovative solutions like biometrics, passkeys, and multi-factor authentication are paving the way for a future where passwords may no longer be the primary means of safeguarding our digital identities.
Embarking into the digital realm has become as routine as sipping my morning coffee.
The constant evolution of technology has seamlessly integrated into every facet of my life, from social interactions to personal finances. Yet, there's one aspect that has become increasingly glaring – the vulnerability of traditional passwords in the face of modern cyber threats.
The digital landscape is a battleground, and the age-old password is fighting a losing battle against the ever-growing sophistication of cyberattacks. It's no secret that we've all been guilty of recycling passwords across various platforms, a habit that's become more perilous with each passing day. As a tech-savvy individual navigating the intricacies of the online world, the gravity of securing my digital identity has never been more palpable.
Enter the era of transformative change in cybersecurity – a paradigm shift away from the archaic reliance on passwords. The buzzwords echo in the corridors of innovation: biometrics, passkeys, multi-factor authentication. These aren't just futuristic concepts; they are the vanguard of a new era where safeguarding our digital identities demands a more robust, user-friendly approach.
Biometrics, with its fingerprint scans and facial recognition, offers a personalized shield that transcends the limitations of alphanumeric combinations. Passkeys, those cryptographic keys dancing in the background, provide an additional layer of security that feels like a digital fortification. And then there's the trusty multi-factor authentication, a dynamic duo or trio that fortifies the fortress, making unauthorized access an uphill battle.
In my day-to-day life, this shift is not merely theoretical; it's a tangible enhancement of my digital security. Gone are the days of fretting over forgotten passwords or the nagging worry of a single point of failure. Instead, my devices recognize me at a glance, and my access is fortified by layers that feel less like a hassle and more like a digital guardian watching over my virtual kingdom.
As technology hurtles forward, I find solace in the fact that the guardians of cybersecurity are adapting in tandem. The traditional password, once the unsung hero of the digital age, is gracefully making way for more sophisticated, intuitive methods. This isn't just progress; it's a necessity in an era where our lives are intricately woven into the fabric of the online world.
So, here as, a young digital denizen, embracing the winds of change in cybersecurity with open arms. The days of passwords as the sole gatekeepers to our digital lives are numbered, and I, for one, am ready for the next chapter in securing our virtual existence. Welcome to the future, where the keys to our digital kingdom are as unique as the fingerprints on our fingertips.
The Inherent Vulnerabilities of Passwords:
Passwords, once the stalwart guardians of our online accounts, are now recognized as inherently insecure. Easily susceptible to theft, guessing, or brute-force attacks, passwords leave users and businesses exposed to a myriad of cybersecurity threats. The common practice of password reuse across multiple accounts exacerbates this vulnerability, providing cybercriminals with a single point of entry to compromise various digital assets.
Password Managers: A Reactive Solution:
While password managers offer a means of organizing and securing passwords, they remain a reactive solution to a fundamental problem. Passwords, by their nature, are weak and outdated, necessitating a more proactive approach to authentication.
Exploring Alternatives:
Several alternative authentication methods are gaining prominence, promising a more secure and seamless user experience.
Biometrics:
Biometrics, encompassing fingerprints, facial recognition, and voice recognition, stand as a formidable alternative to passwords. The uniqueness of biometric data makes it inherently more secure, eliminating the risk of theft or replication.
Imagine you are unlocking your smartphone.
You raise your phone to your face.
Your phone scans your face and recognizes you.
Your phone is unlocked.
This is an example of facial recognition, a type of biometrics that uses the unique features of a person's face to verify their identity.
Distinguishing Between Biometric Identification and Authentication:
Biometric identification employs characteristics like fingerprints, facial features, or retina scans to recognize an individual, whereas biometric authentication utilizes these biometric traits to confirm the claimed identity of a person.
Biometric identification is the process of recognizing individuals based on unique biological or behavioral traits, such as fingerprints, facial features, or iris scans. The primary goal is to establish the identity of a person.
Biometric authentication, on the other hand, uses these biometric traits to verify that individuals are who they claim to be. It involves comparing the presented biometric data (e.g., fingerprint or facial scan) with stored reference data to authenticate the person's identity.
In essence, biometric identification is about recognizing an individual, while biometric authentication is about confirming and validating that recognized identity. Identification is typically the first step in a system, determining who the person is, and authentication follows to ensure the claimed identity is accurate.
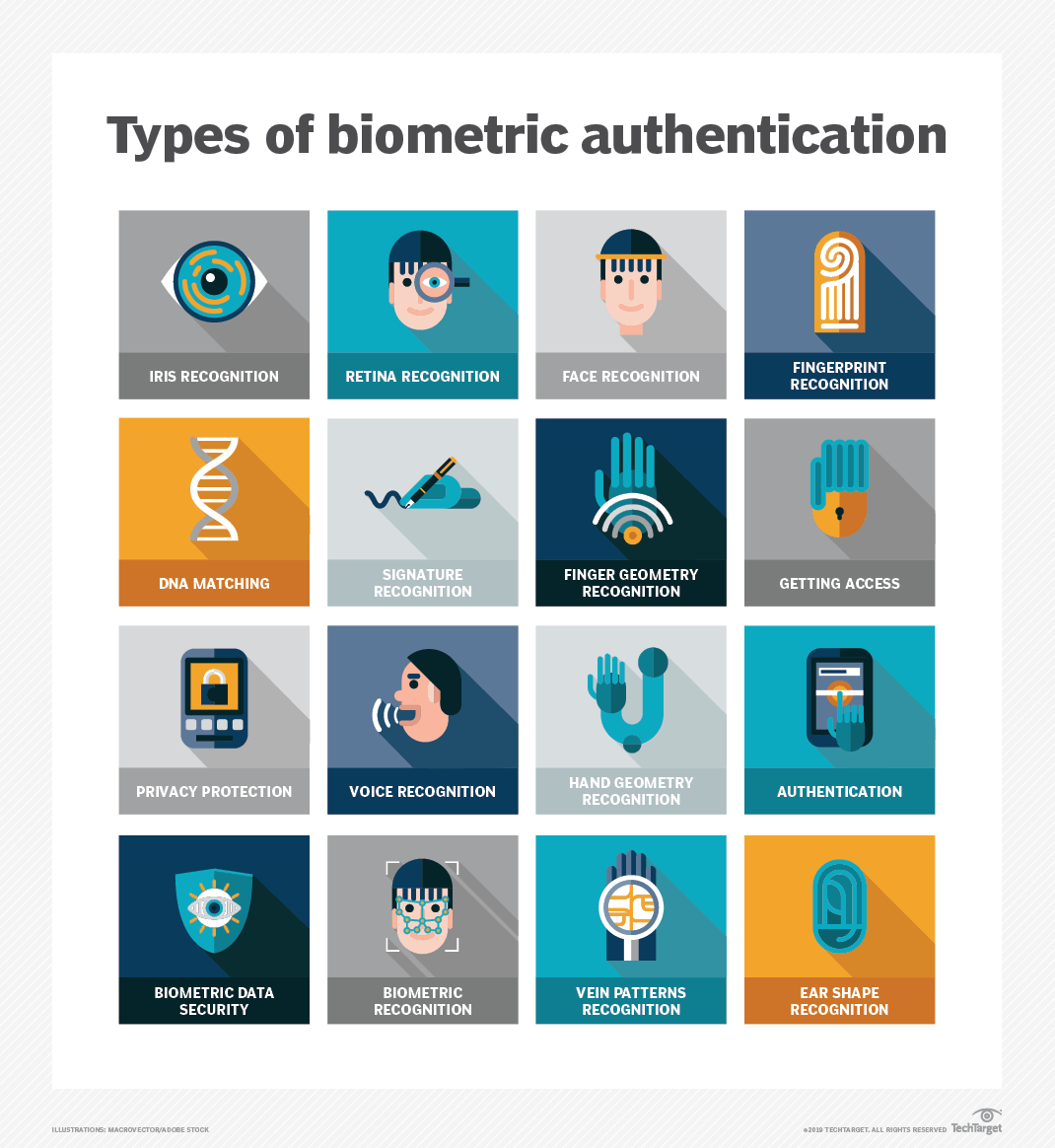
Biometric authentication methods include fingerprint recognition, facial scans, iris or retina scans, voice recognition, palmprint analysis, behavioral biometrics (typing rhythm, mouse movements), vein pattern recognition, ear shape analysis, gait recognition, and, less commonly, DNA biometrics. Each method utilizes unique biological or behavioral traits for secure identity verification.
Biometrics are also used to verify identity in a variety of other contexts, including:
Border control: Biometrics are used to verify the identity of travelers at border crossings.
Law enforcement: Biometrics are used to identify criminals and suspects.
Physical access control: Biometrics are used to control access to buildings and secure areas.
Logical access control: Biometrics are used to control access to computer systems and networks.
Time and attendance: Biometrics are used to track employees' hours worked.
Passkeys:
Passkeys, grounded in public-key cryptography, represent a paradigm shift from traditional password-based authentication. Uniquely generated for each user and immune to reuse across multiple accounts, passkeys offer a decentralized and secure authentication solution.
Imagine you are logging into your online shopping account.
You visit the online shopping website and click on the "Login" button.
You are presented with a list of authentication options, including "Password" and "Passkey."
You select the "Passkey" option and your smartphone vibrates.
You unlock your smartphone and tap on the notification that appears.
You are automatically logged into your account.
This is an example of how passkeys can be used to authenticate to an online account. Passkeys are a new type of authentication that is based on public-key cryptography. This means that instead of using a password, you use a cryptographic key that is unique to your device and the website or app you are logging into.
Passkey authentication process
When you log into an account using a passkey, the website or app will send a challenge to your device. Your device will then use its cryptographic key to sign the challenge and send it back to the website or app. The website or app will then validate the signature to ensure that it is authentic.
Here are some of the key features of passkeys:
Uniquely generated for each user: Passkeys are uniquely generated for each user and account, so they cannot be reused. This makes them much more secure than passwords, which are often reused across multiple accounts.
Decentralized storage: Passkeys are not stored in a central location, so they are not vulnerable to data breaches. Instead, they are stored on the user's device and are only used when the user is logging in to a specific website or app.
Secure verification: Passkeys are verified by the user's device, so they cannot be tricked into being sent to a fake website. This makes them much more resistant to phishing attacks than passwords.
User-friendly authentication: Passkeys are more user-friendly than passwords because they do not require users to remember or type in a password. Instead, users can simply authenticate themselves using their fingerprint, facial recognition, or other biometric factors.
Passkeys are a promising new technology that has the potential to revolutionize the way we authenticate ourselves online. They are more secure than passwords, more user-friendly, and more resistant to phishing attacks. As a result, they are likely to be widely adopted in the coming years.
Passkeys are still under development, but they are expected to be widely adopted in the coming years. They are already supported by a number of major companies, including Google, Apple, and Microsoft.
Here are some of the key features of passkeys:
Uniquely generated for each user and account: Passkeys are uniquely generated for each user and account, so they cannot be reused. This makes them much more secure than passwords, which are often reused across multiple accounts.
Decentralized storage: Passkeys are not stored in a central location, so they are not vulnerable to data breaches. Instead, they are stored on the user's device and are only used when the user is logging in to a specific website or app.
Secure verification: Passkeys are verified by the user's device, so they cannot be tricked into being sent to a fake website. This makes them much more resistant to phishing attacks than passwords.
User-friendly authentication: Passkeys are more user-friendly than passwords because they do not require users to remember or type in a password. Instead, users can simply authenticate themselves using their fingerprint, facial recognition, or other biometric factors.
Passkeys are a promising new technology that has the potential to revolutionize the way we authenticate ourselves online. They are more secure, user-friendly, and resistant to phishing attacks than passwords. As a result, they are likely to be widely adopted in the coming years.
Multi-Factor Authentication (MFA):
MFA introduces an additional layer of security by requiring users to provide multiple forms of verification. This typically involves combining something they know (e.g., a password), something they have (e.g., a mobile phone), and something they are (e.g., a fingerprint). MFA significantly raises the bar for attackers, making it more challenging to compromise user accounts.
Imagine you are logging into your online bank account.
You enter your username and password.
The bank sends a six-digit code to your registered mobile phone.
You enter the six-digit code on the bank's website.
You are now logged into your account.
This is an example of two-factor authentication (2FA), a type of MFA that requires users to provide two pieces of evidence to verify their identity. In this case, the two pieces of evidence are your password and the six-digit code sent to your phone.
MFA is more secure than single-factor authentication (SFA), which only requires users to provide one piece of evidence, such as a password. This is because MFA makes it more difficult for attackers to gain access to a user's account, even if they have stolen the user's password.
For example, if an attacker steals your password, they will still need to steal your phone in order to log into your bank account. This is because the six-digit code sent to your phone is only valid for a short period of time and cannot be reused.
MFA can be implemented in a variety of ways, including:
SMS-based MFA: This is the most common type of MFA, and it involves sending a six-digit code to the user's registered mobile phone.
Email-based MFA: This is another common type of MFA, and it involves sending a six-digit code to the user's registered email address.
Hardware tokens: These are physical devices that generate one-time passwords that can be used to verify a user's identity.
Biometric MFA: This type of MFA uses biometric factors, such as fingerprints or facial recognition, to verify a user's identity.
MFA is a valuable security tool that can help to protect your online accounts from unauthorized access. It is recommended that you enable MFA on all of your online accounts, including your bank accounts, email accounts, and social media accounts.
Here are some of the benefits of using MFA:
Increased security: MFA makes it more difficult for attackers to gain access to your online accounts.
Reduced risk of phishing: MFA can help to protect you from phishing attacks, which are attempts to trick you into revealing your personal information.
Peace of mind: Using MFA can give you peace of mind knowing that your online accounts are protected.
Industry Initiatives and Accelerating Trends:
Recognizing the need for a passwordless future, major companies like Microsoft have taken bold steps in enabling passwordless authentication for their customers. The shift away from passwords is gaining momentum, driven by a collective effort to enhance security, user experience, and cost-effectiveness.
Benefits of Passwordless Authentication:
The advantages of transitioning away from passwords extend beyond mere security improvements. Passwordless authentication brings forth a host of benefits:
Increased Security:
Passwordless methods, such as biometrics and passkeys, are inherently more secure, reducing the susceptibility to cyber threats.
Improved User Experience:
Passwordless authentication offers a more user-friendly experience, eliminating the need to remember complex passwords and easing the burden on users.
Reduced Costs:
Businesses can realize cost savings by implementing passwordless authentication, as it reduces the volume of help desk tickets related to password resets.
Conclusion:
The era of passwords as the primary method of authentication is gradually giving way to more secure, innovative alternatives. Biometrics, passkeys, and multi-factor authentication are shaping a future where digital identities are safeguarded with heightened security measures and improved user experiences. As businesses and users alike embrace these advancements, the journey towards a passwordless authentication landscape is poised to accelerate, ushering in a new era of digital security.